Configuring LDAP Servers
The LDAP Servers table lets you configure up to
The following procedure describes how to configure an LDAP server through the Web interface. You can also configure it through ini file [LdapConfiguration] or CLI (configure system > ldap-configuration).
When you configure an LDAP server, you need to assign it an LDAP Server Group. Therefore, before you can configure an LDAP server in the table, you must first configure at least one LDAP Server Group in the LDAP Server Groups table (see Configuring LDAP Server Groups).
| ➢ | To configure an LDAP server: |
| 1. | Open the LDAP Servers table (Setup menu > IP Network tab > AAA Servers folder > LDAP Servers). |
| 2. | Click New; the following dialog box appears: |
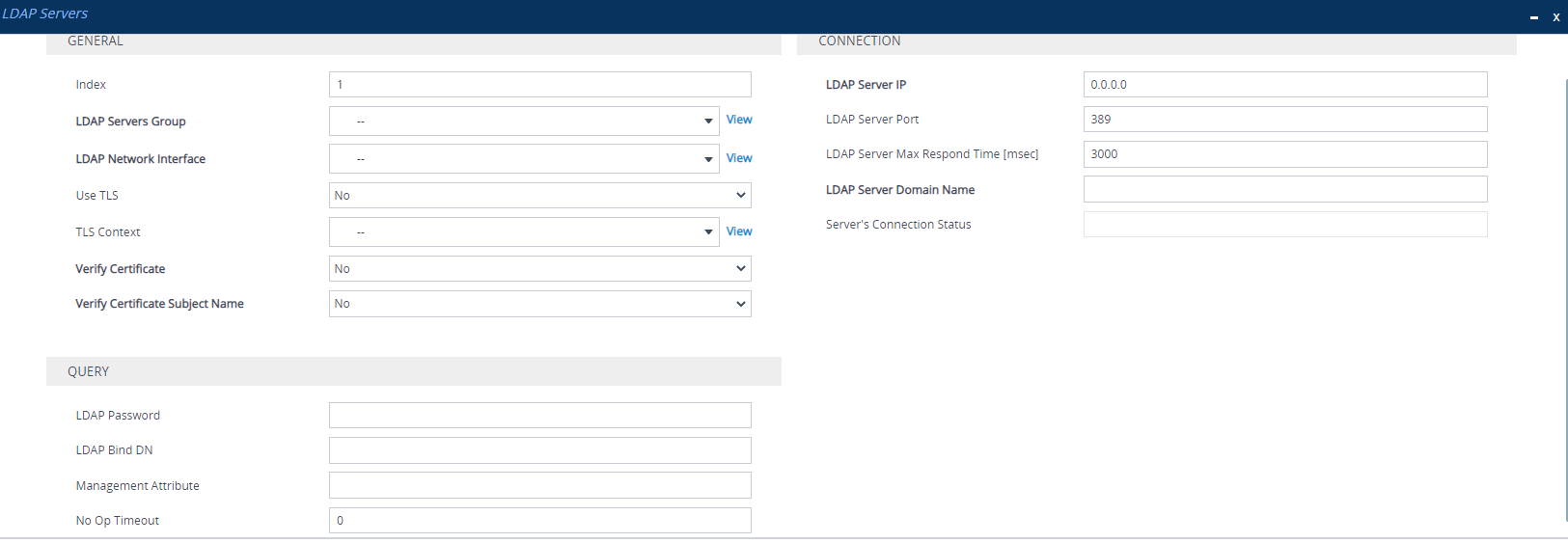
| 3. | Configure an LDAP server according to the parameters described in the table below. |
| 4. | Click Apply. |
LDAP Servers Table Parameter Descriptions
|
Parameter |
Description |
|||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| General | ||||||||||||||||
|
'Index' [Index] |
Defines an index number for the new table row. Note: Each row must be configured with a unique index. |
|||||||||||||||
|
'LDAP Servers Group' server-group [Group] |
Assigns the LDAP server to an LDAP Server Group, configured in the LDAP Server Groups table (see Configuring LDAP Server Groups). Note:
|
|||||||||||||||
|
'LDAP Network Interface' interface-type [Interface] |
Assigns one of the device's IP Interfaces (see Configuring IP Network Interfaces) through which communication with the LDAP server is done. By default, no value is defined and the device uses the IPv4 OAMP interface. Note:
|
|||||||||||||||
|
'Use TLS' use-tls [useTLS] |
Enables the device to encrypt the username and password (for Control and Management related queries) using TLS when sending them to the LDAP server.
|
|||||||||||||||
|
'TLS Context' tls-context [ContextName] |
Assigns a TLS Context (TLS configuration) for the connection with the LDAP server. By default, no value is defined and the device uses the default TLS Context (ID 0). To configure TLS Contexts, see Configuring TLS Certificates. Note: The parameter is applicable only if the 'Use TLS' parameter is configured to Yes. |
|||||||||||||||
|
'Verify Certificate' verify-certificate [VerifyCertificate] |
Enables certificate verification when the connection with the LDAP server uses TLS.
Note: The parameter is applicable only if the 'Use TLS' parameter is configured to Yes. |
|||||||||||||||
|
'Verify Certificate Subject Name' verify-subject-Name [VerifySubjectName] |
Enables the verification of the TLS certificate subject name (Common Name / CN or Subject Alternative Name / SAN) that is used in the incoming connection request from the LDAP server.
Note: The parameter is applicable only if the 'Use TLS' parameter is configured to Yes. |
|||||||||||||||
|
Connection |
||||||||||||||||
|
'LDAP Server IP' server-ip [LdapConfServerIp] |
Defines the IP address (IPv4 or IPv6) of the LDAP server. By default, no IP address is defined. Note:
|
|||||||||||||||
|
'LDAP Server Port' server-port [LdapConfServerPort] |
Defines the port number of the LDAP server. The valid value range is 0 to 65535. The default port number is 389. |
|||||||||||||||
|
'LDAP Server Max Respond Time' max-respond-time [LdapConfServerMaxRespondTime] |
Defines the duration (in msec) that the device waits for LDAP server responses. The valid value range is 0 to 86400. The default is 3000. Note:
|
|||||||||||||||
|
'LDAP Server Domain Name' domain-name [LdapConfServerDomainName] |
Defines the domain name (FQDN) of the LDAP server. The device tries to connect to the LDAP server according to the IP address listed in the received DNS query. If there is no connection to the LDAP server or the connection to the LDAP server fails, the device tries to connect to the LDAP server with the next IP address in the DNS query list. Note:
|
|||||||||||||||
|
'Server's Connection Status' connection-status [ConnectionStatus] |
(Read-only) Displays the connection status with the LDAP server.
For more information about a disconnected LDAP connection, see your syslog messages generated by the device. Note: When the LDAP server is assigned to an LDAP Server Group that is for management (see Configuring LDAP Server Groups), the connection status of the LDAP server is always "Not Applicable". |
|||||||||||||||
|
Query |
||||||||||||||||
|
'LDAP Password' password [LdapConfPassword] |
Defines the user password for accessing the LDAP server during connection and binding operations. The valid value of the parameter depends on the type of LDAP Server Group (defined by the 'Type' parameter in the LDAP Server Groups table):
Note:
|
|||||||||||||||
|
'LDAP Bind DN' bind-dn [LdapConfBindDn] |
Defines the LDAP server's bind Distinguished Name (DN) or username.
Note: By default, the device sends the username in clear-text format. You can enable the device to encrypt the username using TLS (see the 'Use TLS' parameter in this table). |
|||||||||||||||
|
'Management Attribute' mgmt-attr [MngmAuthAtt] |
Defines the LDAP attribute name to query, which contains a list of groups to which the user is a member. For Active Directory, this attribute is typically "memberOf". The attribute's values (groups) are used to determine the user's management access level; the group's corresponding access level is configured in Configuring Access Level per Management Groups Attributes. Note:
|
|||||||||||||||
|
'No Op Timeout' noop-timeout [NoOpTimeout]
|
Defines the timeout (in minutes) of inactivity in the connection between the device and the LDAP server, after which the device sends an LDAP "abandon" request to keep the LDAP connection alive (i.e., LDAP persistent connection). The valid value to enable this feature is any value greater than 0. The default is 0 (i.e., if there is no activity on the connection, the device doesn't send "abandon" requests and the LDAP server may disconnect). Note: The parameter is applicable only to LDAP connections that are used for routing (i.e., the 'Type' parameter is configured to Control). |
|||||||||||||||